2021 Top Cloud Security Tools For Business
By Laura Cowan
Laura K. Cowan is a tech, business, and wellness journalist and fantasy author whose work has focused on promoting sustainability initiatives and helping individuals find a sense of connection with the natural world.
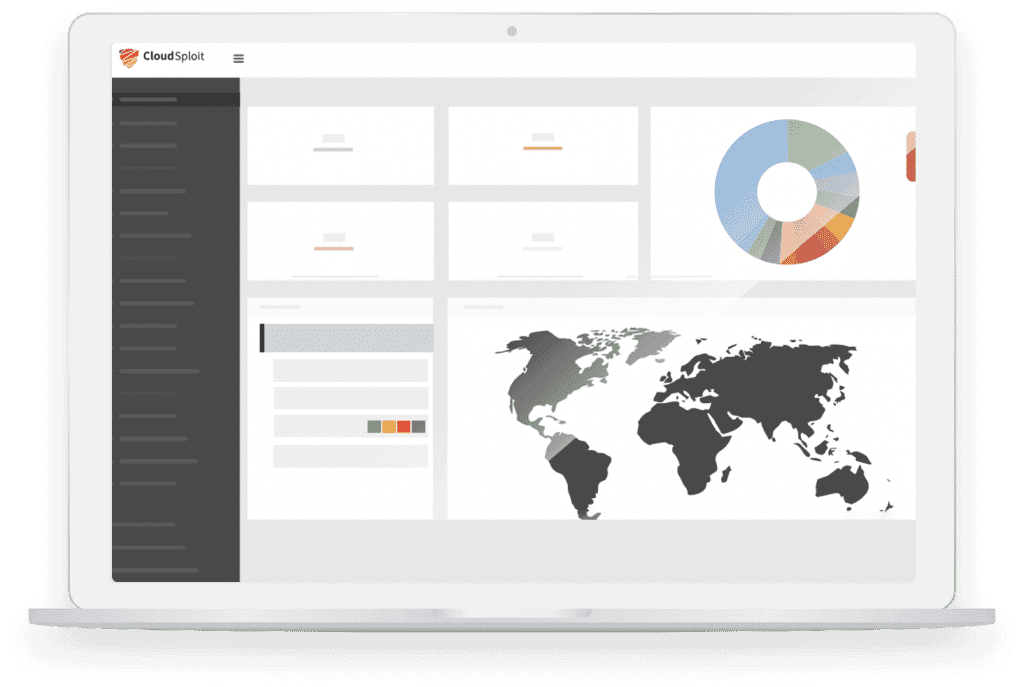
CloudSploit offers visual cybersecurity monitoring tools for business.
This post is sponsored by cloud consulting firm Trek10, who support businesses by migrating their data to the cloud and protecting them from security threats. All content and views expressed are those of the participants and do not necessarily reflect those of Trek10. If you would like to sponsor news coverage of tech companies and trends in your industry or region, please contact the editor.
So you know that the COVID-19 pandemic introduced a wave of new security risks for your business, but how do you get eyes on the problem? How do you assess security risks? Comparitech lists tools such as CloudStrike Falcon and Barracuda CloudGen Firewall as its top recommendations for cloud security tools, but the list goes on from there. There are so many choices, and they all do something a little different.
How do you choose a cloud security monitoring service for your business? If you're struggling to get eyes on your security vulnerabilities in a rapidly changing business climate, you're not alone. We wanted to put together a behind the scenes explanation for you on what to look for in a security monitoring tool, so you know you're making the best decision for your business.
Trek10 cloud security engineer Chris Beaufils sat down with us this week to talk about security tools your business can use to track security risks. Some of these tools are used by Trek10 with clients to help them monitor security risks to their assets in real-time and can be combined.
Top Cloud Security Tools For Business
CloudSploit
CloudSploit is a cloud security as a service tool that monitors the security of your assets across AWS, Azure, and Google Cloud. Beaufils says he recommends CloudSploit as a security monitoring tool because "it's an effective tool that enables people to customize it to their application" and because CloudSploit offers visual tools that are easy to use. Beaufils says CloudSploit helps people learn best practices and find vulnerabilities they might not be aware of. It's not a full-scope tool, but allows clients to continuously scan for vulnerabilities.
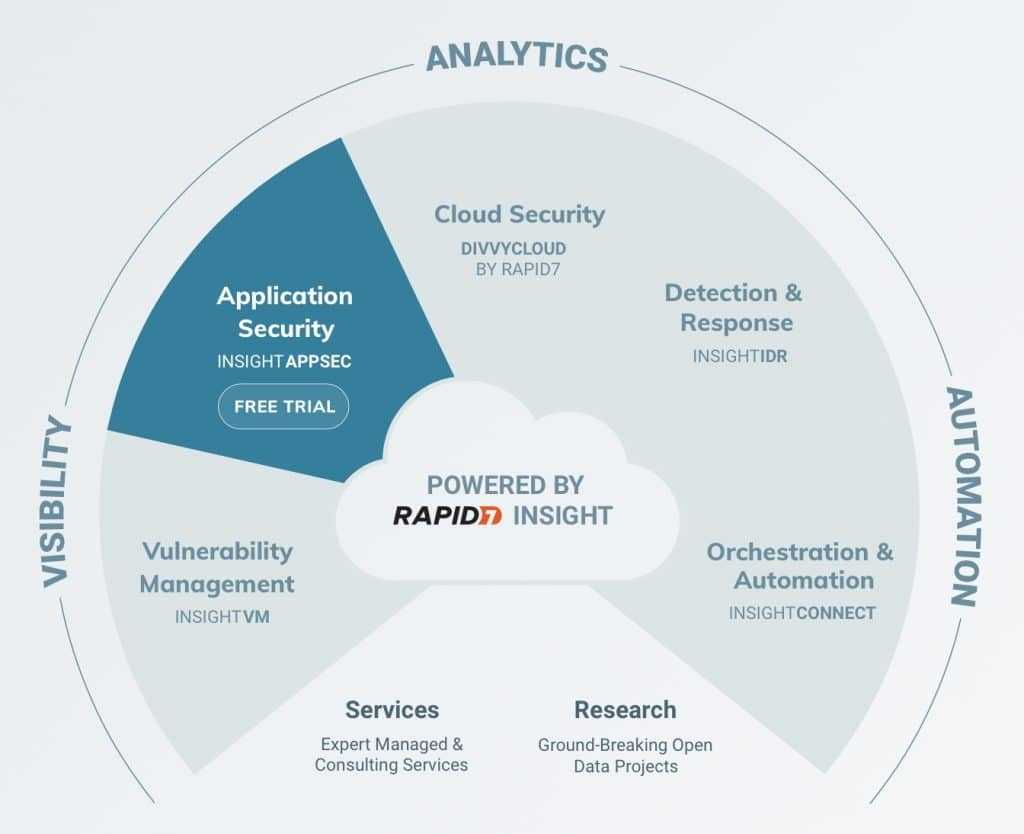
Rapid7's cybersecurity analytics brings together vulnerability management, application security and cloud security, and automation.
Rapid7
Rapid7 offers cybersecurity and compliance solutions that can automate some of your cloud security threat monitoring. It's used by 8,900 corporate clients including Revlon, Domino's, Univision, and The Washington Post. Beaufils says you can "use Rapid7 to do port scanning," which is a method of determining which ports on a network are open and could be sending or receiving data and might need to be secured. Like many other security firms, Rapid7 automates some aspects of security monitoring, which can make security monitoring more efficient and cost effective.
DataDog
DataDog is another cloud monitoring as a service operation that's popular to monitor "any stack, any app, at any scale, anywhere." Whole Foods, 21st Century Fox, and Peloton use DataDog, and Trek10 is a DataDog partner, working with their tools to help monitor client security issues for their cloud-hosted data. Gartner Research listed DataDog as a 2021 Leader in the Gartner Magic Quadrant for Application Performance Monitoring. "We use DataDog as part of our 24/7 monitoring," Beaufils says. "Sometimes clients use it with us." This brings up an important point: how involved should you be in your own security monitoring for assets hosted on the cloud?
DataDog helps you see your infrastructure in terms of security threats, and offers a variety of threat monitoring services.
How Do You Choose a Cloud Monitoring Tool For Your Business?
How do you choose which cloud security tool is right for your business? Do you use just one tool, or combine them? Should you monitor yourself, or have someone do it for you?
Security solutions are about putting together a suite of tools that can keep an eye on your specific assets. Sometimes that's focused on a particular software application you're creating and making sure it's secure. Sometimes a business is concerned about their data being secure when workers are remote. It depends on your type and size of business, and the different tools that have to work together to send and receive data while operating together securely.
The Trek10 team at work.
Beaufils has this recommendation for sorting it all out: the key to choosing a cloud security tool or consulting firm is knowing what kind of partnership you want. Do you need an extension to an existing security team? Staff augmentation that equals having 1-2 extra people focused on security? Or do you need a response team for emergency data breaches? The good news about the complex topic of cloud security these days is that there are so many scalable options for security monitoring. The trick is figuring out which assets need monitoring and what type of monitoring and response is helpful for your situation.
Sometimes it can help to have an independent review to help you get eyes on the problem. If you're interested in a security assessment for your business, our sponsor for this series, Trek10, is offering a free security assessment this month to help you customize a solution.
Our thanks to Trek10 for their generous sponsorship of news coverage in the cloud computing and cybersecurity space. To learn more about advertising and content sponsorship opportunities with Cronicle Press Tech News, please visit our Sponsorship page or contact the editor for more details on sponsorship opportunities.
business cybersecurity tools, cloud security, cybersecurity, security for business, trek10